
Why You Should Prioritize Your Technology Gaps
Technology is an unavoidable component of most businesses these days, helping them achieve their goals and vision. However, if you are not cautious, technological flaws

Technology is an unavoidable component of most businesses these days, helping them achieve their goals and vision. However, if you are not cautious, technological flaws

In this day and age, technology, slowly and steadily, is taking over our lives, hence a lot of pressure has been placed upon it. Every

A security incident can topple an organization’s reputation and revenue in a short amount of time. As billionaire Warren Buffet once said, “it takes 20

Law firms need effective and flawless forms of communication. This is a requirement to build a long-lasting and healthy relationship between a client and the
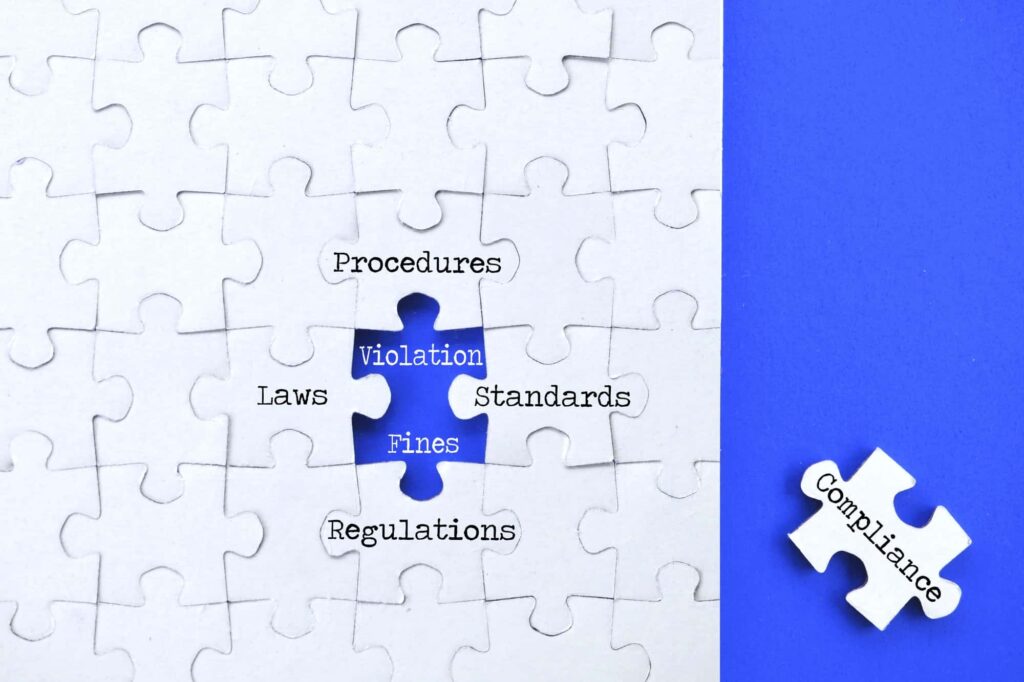
The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive move by the U.S. Department of Defense (DoD) that involves a lot of moving parts that

Tools are only as good as their users. This should be your guiding philosophy as the world shifts to a hybrid work model to deal

Security is the main concern for almost every business. In this world, where hackers have become smarter day and day. They have developed new tactics

The only way to prevent your employees from compromising your business data is by providing regular security awareness training. Conducting a one-time training program will

Backup should be a part of every organization’s business strategy, irrespective of its size, location or industry. Threats to business data are very real and

Critical Infrastructure (CI) comprises physical and cyber assets vital for the smooth functioning of societies and nations across the globe. The sectors that make up
Take back your time with our 82% first-call resolution rate—quick, efficient IT support that keeps your business running smoothly.
Let’s solve your tech issues the first time!