
Reasons why your New York Company needs a Locally based Manhattan IT Support company
As a business owner in New York, you have many responsibilities. One of the most important is ensuring that your company’s technology is up-to-date and

As a business owner in New York, you have many responsibilities. One of the most important is ensuring that your company’s technology is up-to-date and

Ransomware attacks are becoming increasingly common, with businesses of all sizes becoming targets. These attacks can cause significant disruption to your business operations and result

Safeguarding your organization’s online assets is critical in today’s digital world. Unfortunately, poor password hygiene practices by some employees cause problems for many small businesses,

A spam blocker or filter prevents unwanted emails to reach your inbox and prevents any consequential harm to your business. Unfiltered enterprise emails can be

Simply described, outsourced IT support is hiring or partnering with a third-party IT support company to handle or maintain all your business technology

It has been said many and many times over, there’s always room for improvement, so why today’s business owners are reluctant to improve their technology

In this day and age, technology, slowly and steadily, is taking over our lives, hence a lot of pressure has been placed upon it. Every
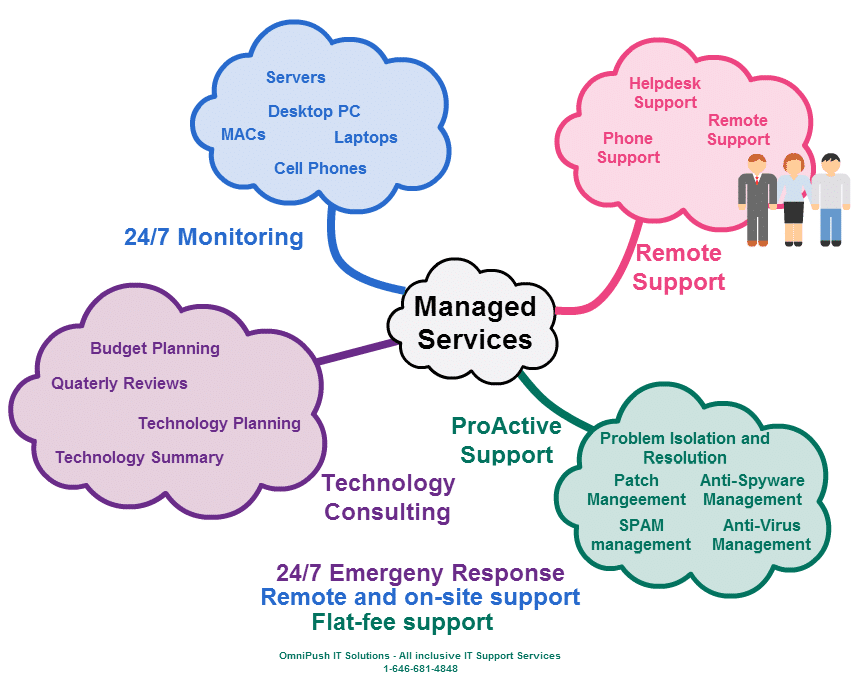
Businesses of all sizes prioritize on operational efficiency and productivity, however, not every business is equipped to maintain this competence. Particularly, small businesses have limited

A security incident can topple an organization’s reputation and revenue in a short amount of time. As billionaire Warren Buffet once said, “it takes 20

Law firms need effective and flawless forms of communication. This is a requirement to build a long-lasting and healthy relationship between a client and the
Take back your time with our 82% first-call resolution rate—quick, efficient IT support that keeps your business running smoothly.
Let’s solve your tech issues the first time!