How a Company Should Handle Ransomware Attacks: Protecting Your Business and Data
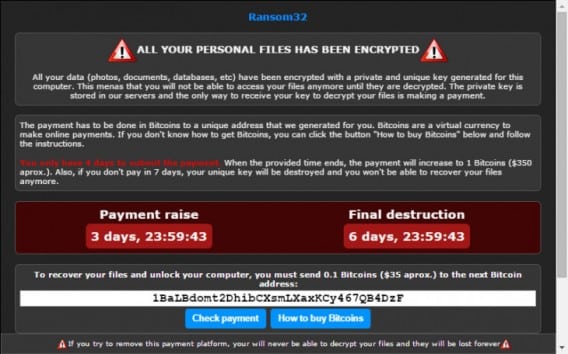
Ransomware attacks are becoming increasingly common, with businesses of all sizes becoming targets. These attacks can cause significant disruption to your business operations and result