Many businesses unknowingly expose themselves to major risks by not fully securing their cloud infrastructure. Cloud security isn’t just about protecting data—it’s about safeguarding your entire digital environment from costly and damaging breaches.
According to Statista, the top cloud security concerns are data loss and leakage (69%), and data privacy/confidentiality (66%), followed by accidental exposure of credentials (44%). Despite being aware of these challenges, only one in five organizations assess their overall cloud security posture in real-time.
As Whawenst Duvet, CTO, OneTech360 says, “Securing your cloud is not an option; it’s a critical component of your business’s success in a digital world.”
Cloud Breaches Are Rising—Are You Prepared?
Let OneTech360 fortify your cloud against risks.
What Is Cloud Security? The Foundation of Your Digital Defense
Cloud security refers to the practices, technologies, and policies put in place to protect your data and systems hosted on the cloud. It’s about ensuring your cloud environment remains secure from both internal and external threats.
According to CloudSecureTech, 48% of businesses store classified and sensitive data on cloud servers, emphasizing the critical need for robust cloud security measures. Without proper safeguards, this data becomes vulnerable to breaches, misconfigurations, and other security threats.
Cloud security is multifaceted: it includes data encryption, firewalls, threat detection, identity management, and regular audits. Think of it as a comprehensive strategy to keep your digital assets safe.
What Is Cloud Computing Security? Safeguarding Your Cloud-Based Systems
Cloud computing security is a critical aspect of cloud security that focuses on securing all aspects of cloud-based infrastructure and services. It involves a set of protections that ensure your business’s data, applications, and systems remain safe while running on cloud platforms.
Key areas include:
- User Authentication: Strong multi-factor authentication to prevent unauthorized access.
- Data Encryption: Encrypting sensitive data both in transit and at rest to keep it protected.
- Regulatory Compliance: Ensuring you meet industry-specific regulations to avoid penalties.
Mastering what is cloud computing security ensures you prevent breaches before they happen.
| More articles you might like: |
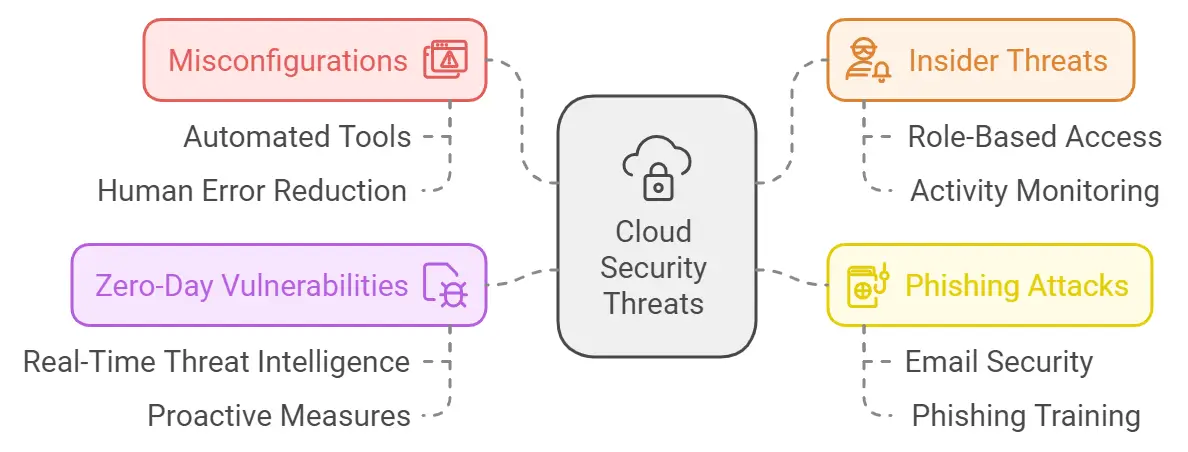
Identifying Cloud Security Threats: The Risks You Can’t Ignore
The cloud, while powerful, is not without its risks. Here are the top threats you need to be aware of:
- Misconfigurations: Cloud environments are complex, and simple mistakes in setup can leave your data exposed.
Solution: Use automated tools to ensure consistent configuration and reduce human error. - Insider Threats: Employees or contractors could intentionally or unintentionally cause harm.
Solution: Limit access based on roles and monitor all internal activity. - Phishing Attacks: Attackers trick users into revealing credentials.
Solution: Implement email security systems and provide regular phishing awareness training. - Zero-Day Vulnerabilities: Hackers exploit vulnerabilities before they’re patched by vendors.
Solution: Utilize real-time threat intelligence and stay ahead of the curve.
Protecting Your Cloud Infrastructure: Security Strategies That Work
1. Strengthening Infrastructure Security in Cloud Computing
When asking what is infrastructure security in cloud computing, you’re addressing the foundation of your cloud protection. This involves securing the physical and virtual infrastructure—such as networks, servers, and storage systems—that supports your cloud environment.
Best Practice Tip:
Implement network segmentation to isolate critical systems from the rest of your network, minimizing the risk of a breach spreading.
2. Protecting Your Data: Data Security in Cloud Computing
Data security is a core pillar of cloud security. It focuses on ensuring that sensitive information remains confidential and protected from unauthorized access.
Out-of-the-Box Strategy:
Use homomorphic encryption, which allows you to process encrypted data without decrypting it, ensuring that your data remains safe even during computations.
3. What Is Cloud Workload Security? Managing Your Business Workloads
Your cloud workloads—applications, databases, and services—are essential to your business operations. Cloud workload security involves protecting these workloads from vulnerabilities, attacks, and misconfigurations.
Actionable Tip:
Use container security to isolate each workload, which prevents a breach in one container from affecting others. Tools like Kubernetes can help manage and secure your workloads effectively.
Avoiding Common Cloud Security Mistakes
1. Overlooking Built-in Security Features
While cloud providers offer built-in security features, they may not be enough for your business’s specific needs. Complement these with third-party tools for enhanced protection.
2. Not Training Your Employees
Humans remain the weakest link in cybersecurity. Failing to educate your team on spotting phishing scams or maintaining strong passwords can lead to serious breaches.
3. Ignoring Regulatory Requirements
Your cloud environment must comply with relevant laws such as GDPR, HIPAA, or PCI-DSS. Ensure regular audits and use automated compliance tools to stay aligned with industry standards.
The Future of Cloud Security: What You Need to Know
As cloud technologies evolve, so do the threats. Here are some trends that will shape the future of cloud security:
- AI-Driven Threat Detection: Artificial intelligence will help detect vulnerabilities and prevent attacks in real time.
- Serverless Security: With the rise of serverless computing, new security tools will focus on securing functions and APIs instead of the traditional server infrastructure.
- Edge Security: As more devices connect to the internet, securing edge networks will become increasingly important.
Key Cloud Security Components: Essential Features and Best Practices
| Cloud Security Component | Key Features | What to Consider |
| Identity and Access Management | Manages user access and roles with Multi-Factor Authentication (MFA) | Ensure MFA is set up for all users and roles to minimize unauthorized access risks. |
| Cloud Encryption | Encrypts data at rest and in transit, protecting sensitive information | Double-check that all sensitive data, including backups, is encrypted in the cloud. |
| Security Monitoring & Logging | Continuous monitoring and logging of activity to detect unusual behavior | Be proactive—set up alerts for any irregularities to quickly address potential threats. |
| Firewall and Network Protection | Virtual firewalls and intrusion detection/prevention systems | Ensure firewalls are configured correctly to protect against internal and external threats. |
| Disaster Recovery | Cloud-based backup and disaster recovery solutions | Implement regular backups and test recovery processes to ensure fast recovery during incidents. |
Protect Yourself from Cloud Security Risks with OneTech360
Cloud security isn’t just a luxury; it’s a necessity for modern businesses. By understanding what is cloud security, cloud computing security, and implementing best practices like strong encryption, workload isolation, and continuous monitoring, you ensure your business can thrive securely in the cloud.
| Discover Trusted Cloud Security Services Near You: | ||
| Scranton | Allentown | Manhattan |
OneTech360 specializes in providing customized cloud security strategies that protect your infrastructure and data. Reach out today for a consultation and secure your cloud environment!



